
From Legacy Systems to Cloud-Native Agility: How Cloud 9 Infosystems Accelerates AWS Modernization
Modernize legacy systems with AWS—secure, scalable, and cloud-native solutions by Cloud 9 Infosystems.
As a Solutions Partner for Security Cloud 9 demonstrates our comprehensive capability to safeguard your organization. We provide integrated security compliance and identity solutions that protect your assets and ensure business continuity.


Ransomware attacks are becoming more sophisticated, with ransom demands doubling from 2021 to 2022, prompting organizations to prioritize advanced Microsoft Cloud Security solutions for proactive threat defense.

The average cost of recovering from a data breach has risen to U.S. $4.35M, putting significant financial pressure on organizations and reinforcing the need for stronger security controls and proactive risk management.

Cybersecurity teams are under growing strain, with 2 in 5 security leaders reporting extreme risk due to ongoing staff shortages, making it harder to manage threats and respond effectively to security incidents.
Implement a Zero trust security model that ensure rigorous identity verification, regardless of the user’s location.
Increase security assurances for your critical business assets
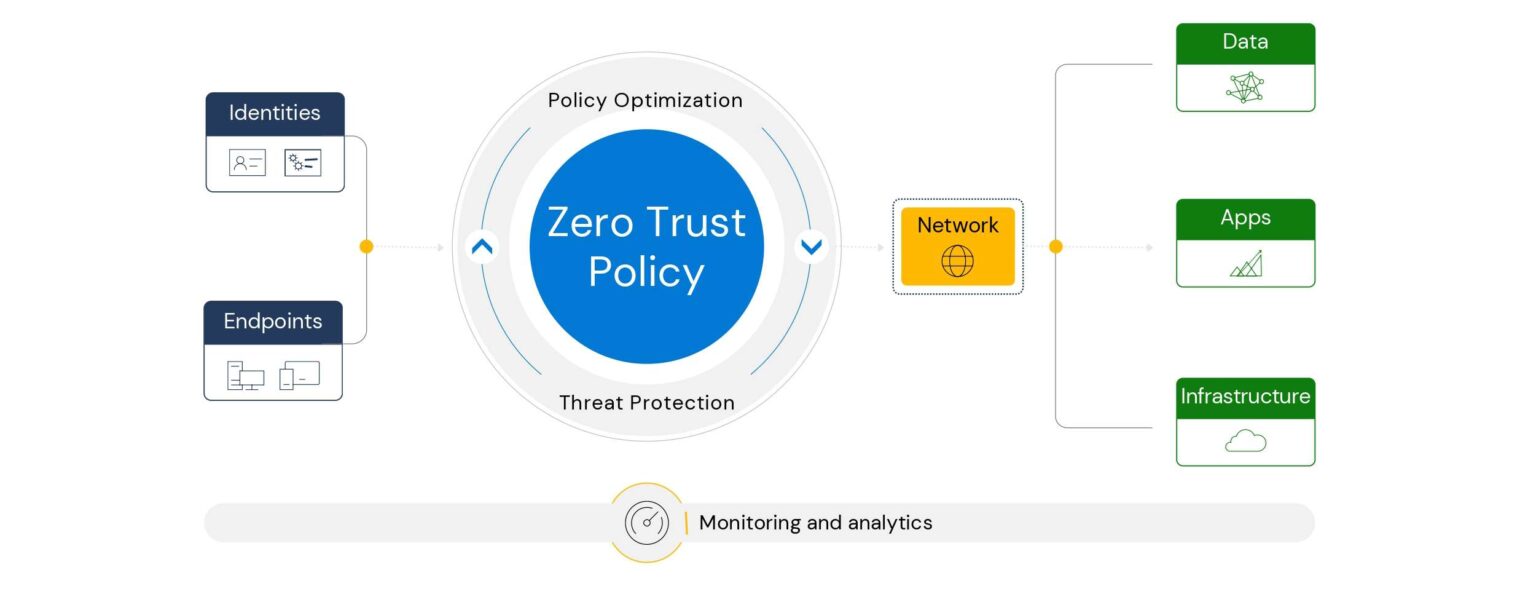
With the rise in security threats and the transition from remote to hybrid work, the Zero Trust framework helps you protect the entire technology ecosystem.

Authenticate and authorize based on all available data points, including user identity, location, device health, service or workload, data classification, and anomalies.

Limit user access with just-in-time and just-enough access (JIT/JEA), risk-based adaptive polices, and data protection to help secure both data and productivity.

Minimize blast radius and segment access. Verify end-to-end encryption and use analytics to get visibility, drive threat detection, and improve defenses.
Use XDR to bring together threat detection, investigation, and response across all data sources.
Get true visibility with incidents that span endpoints, identities, email, collaboration tools, SaaS apps, data loss insights, and cloud.
Detect cyberthreats faster with Microsoft cyberthreat data informed by 65 trillion diverse daily signals for insights into a broad set of cyberthreat vectors
Integrate across domains to defend against threats, using AI and automation to enhance detection and response capabilities.
Native integration across domains




Enhances Threat Protection and Response: Achieve real-time threat detection and response, reducing the risk of significant security breaches.
Cost Efficiency: Emphasize potential savings from using cloud-native SIEM solutions like Microsoft Sentinel, which offers integrated threat intelligence and simplified operations.
Compliance and Risk Management: Improved compliance with data protection regulations and reduced operational risks due to enhanced security measures.

ROI over three years

less expensive
compared to prem SIEMs

reduction in management effort for infrastructure and SIEM


decrease in time
to deployment with pre-built SIEM content and
out-of-the box functionality

reduction in investigation effort

decrease in false positives over three years





1.A commissioned study conducted by Forrester Consulting, “The Total Economic ImpactTM of Microsoft Azure Sentinel,” November 2020. Results are for a composite organization..
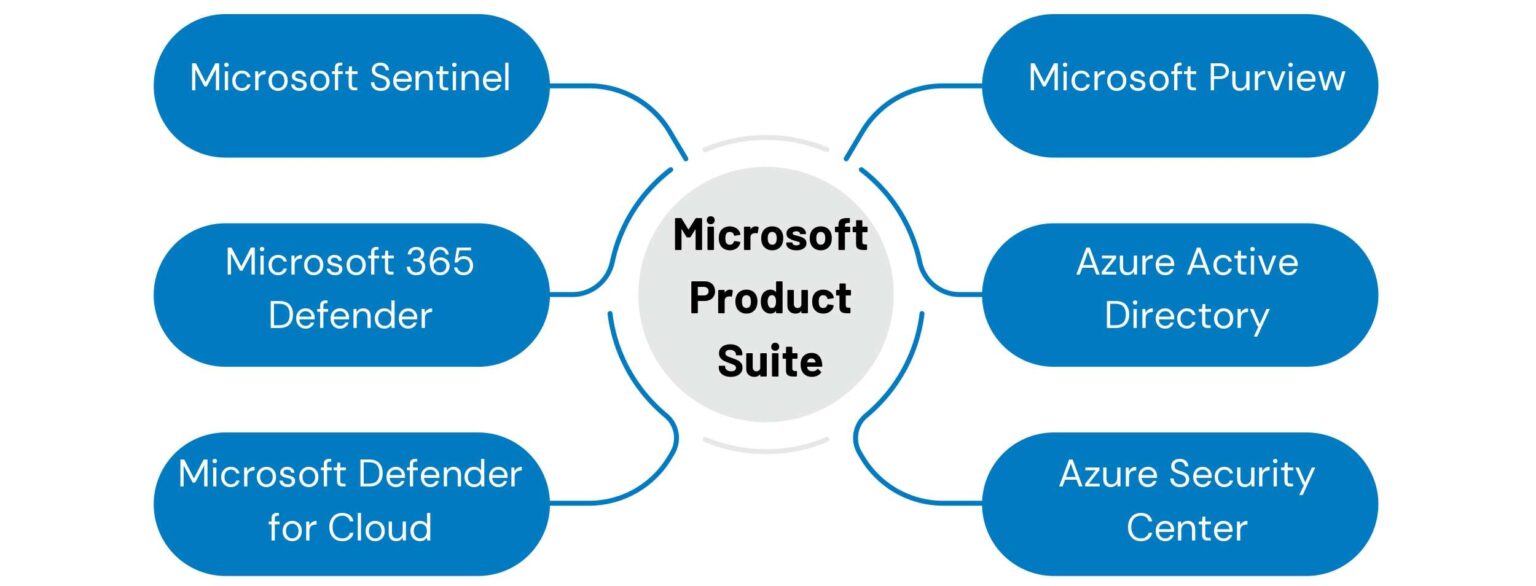
Our IT security expertise supports a
wide range of Microsoft
technologies.


Modernize legacy systems with AWS—secure, scalable, and cloud-native solutions by Cloud 9 Infosystems.

Cloud cost optimization is now a strategic priority for IT leaders. Discover proven best practices to reduce cloud spend by 20–30%, improve cost visibility, and maintain performance across AWS, Azure, and multi-cloud environments.
Discover how Azure AI Foundry enables enterprises in India to operationalize AI agents securely, govern them effectively, and scale AI without compliance risk.
Error: Contact form not found.
